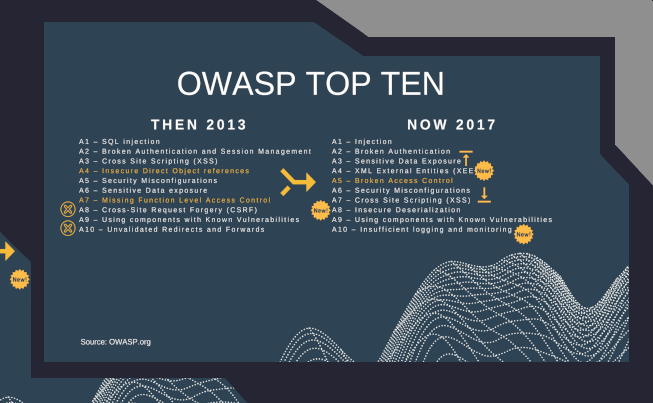
Vision
To be the most trusted and preferred partner in IT industry and by providing most secure internal processes, solution to the customer for their specific information security requirements.
Details

Mission
Our passion and entrepreneurial culture will ensure that we deliver safety, quality and assurance – today and in the future for our customers. Our values are a set of beliefs that guide our behavior and help us to deliver our mission.
Details